CrowdStrike Dtech Info
DTech IT Service Desk Knowledge Base
CrowdStrike - Antivirus
About the CrowdStrike Falcon Platform
What is Falcon?
CrowdStrike Falcon is a SaaS-based, next generation endpoint protection solution that provides advanced detection, prevention, monitoring and search capabilities, allowing analysts to defend against sophisticated threats and adversaries. Falcon offers remote visibility across endpoints throughout an environment, enabling instant access to the "who, what, when, where, and how" of an attack. We collect and analyze more than 80 billion endpoint events each day from millions of sensors deployed across 176 countries. Falcon can help you protect your endpoints, whether you have just a few or hundreds of thousands.
How does Falcon work?
Falcon consists of two components: the sensor and the cloud.
First, a lightweight sensor is deployed to every endpoint where it gathers appropriate system events from each host and takes proactive detection and prevention actions. The Falcon sensor detects and defends against attacks occurring on disk and in memory. The platform continuously watches for suspicious processes, events, and activities, wherever they may reside. Falcon also provides advanced prevention capabilities like custom whitelisting, custom blacklisting, malware blocking, exploit blocking, and IOA-based prevention (Indicators of Attack).
Data gathered by the sensor is then transmitted continuously from the sensor to CrowdStrike's Advanced Threat Intelligence Cloud, where CrowdStrike analyzes and draws links between events across the entire Falcon sensor community. These behavioral patterns are detected in real time via CrowdStrike's Threat Graph data model, allowing analysts to detect new attacks, whether the attacks use malware or not.
CrowdStrike provides you a suite of powerful investigation, prevention, detection, and sensor monitoring tools in the Falcon web interface—your command center for everything to do with Falcon. See the Falcon Console User Guide for an app-by-app walkthrough.
What detection capabilities does Falcon have?
For known threats, Falcon provides cloud-based antivirus (Cloud AV) and Indicators of Compromise (IOC) detection capabilities. For unknown and zero-day threats, Falcon applies IOA detection, using machine learning techniques to build predictive models that can detect never-before-seen malicious activities with high accuracy. Driven by CrowdStrike's Threat Graph data model, this IOA analysis recognizes behavioral patterns to detect new attacks.
Frequently Asked Questions (FAQ):
Why is there no manual scan button?
Traditional antivirus products rely primarily on signature-based on-access scans (OAS) of the file system (scan on file reads and/or on file writes). Signature-based detection is by definition reactive, so anything new/unknown to the signature that was loaded at the time of the scan will likely go undetected. In addition, since OAS is scanning on read/write, if it can't detect the risk from a malicious file at that moment, the file may also go undetected if and when it's executed. To mitigate the risk inherent in that reactive model, traditional AV adds the on-demand scan (ODS) option so you can re-scan previously scanned files with a newer signature in the hope of detecting them later, and with luck prior to them being executed. That model of operation also adds significant overhead to every computer, and typically requires adding a lot of file/folder exclusions to avoid file-contention-based corruption risks, and also to prevent significant reduction in system performance.
Instead of scanning the file system on reads/writes, CrowdStrike Falcon monitors executable's using behavior-based detection – our machine-learning and IOA detection's are thus primarily proactive rather than reactive, and without the overhead of traditional AV. Falcon is better equipped to detect previously unknown/zero-day threats. There's no need to repeatedly scan the file system in advance of file execution, because we always scan on execution – a file which is simply sitting on a disk but is never executed presents no active threat.
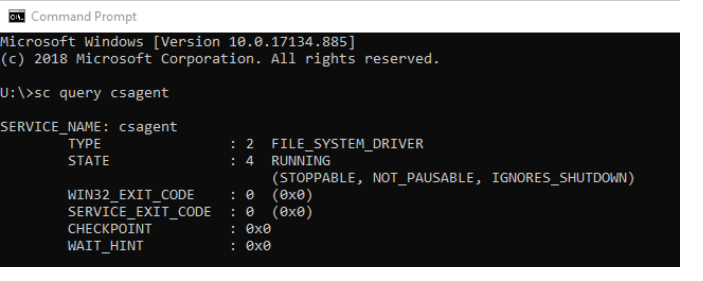
How do I know CrowdStrike is running?
- Open Command Promp
- Input "SC query csagent" and hit enter
- csagent state should be RUNNING
How do I install/uninstall the software?
CrowdStrike Falcon Sensor Install & Removal
What if CrowdStrike is blocking a file or application I need?
Whenever it is identified that a file or application is being blocked by CrowdStrike that the end user believes is a non-threat or is non-malicious a Jira ticket should be created and assigned to the NSOC Support Group.
This ticket must include the following:
- Reporter contact information
- File/Application name
- Where the file originated from (email, website, software repository, etc.)
- Impacted systems
- Impacted users
- Business need
The NSOC will then conduct an evaluation of the file/application to verify the accuracy of the automated detection. If the file is deemed non-malicious a temporary white list will be enacted until the vendor has a chance to adjust their detection mechanism. Files that are determined malicious will not be white listed unless the Chief Information Security Office authorizes the change. All white lists will be reviewed annually.
Clearing Cache and Cookies
CrowdStrike Falcon Sensor Install & Removal Powered by Atlassian Confluence and Scroll Viewport.
